Passwords are one of the weakest links in cybersecurity. With phishing attacks and credential leaks on the rise, Microsoft 365 now supports passwordless authentication through Entra ID (formerly Azure Active Directory). This guide walks you through how to enable passwordless sign-in using Microsoft Authenticator.
Why Passwordless?
Passwordless authentication improves security, simplifies user access, and reduces IT support tickets. It also aligns with zero-trust security frameworks, helping your organization stay ahead of compliance requirements. Plus it's incredibly satisfying to use (or maybe that's just me).
What You'll Need
- Microsoft 365 with Entra ID access
- Admin permissions in your Microsoft tenant
- Multi-Factor Authentication (MFA) enabled
- Microsoft Authenticator app installed on users' devices
Step 1: Enable Passwordless Sign-In in Entra ID
- Sign in at https://entra.microsoft.com
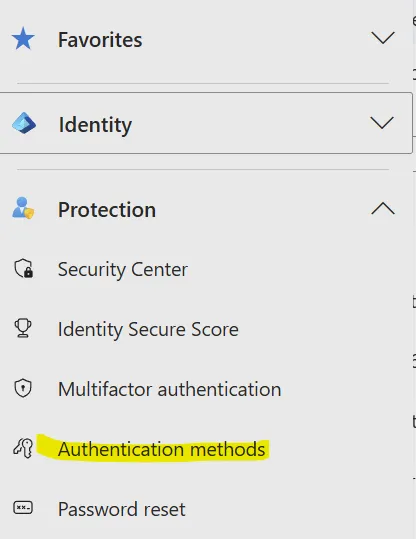
- Navigate to: Protection > Authentication methods
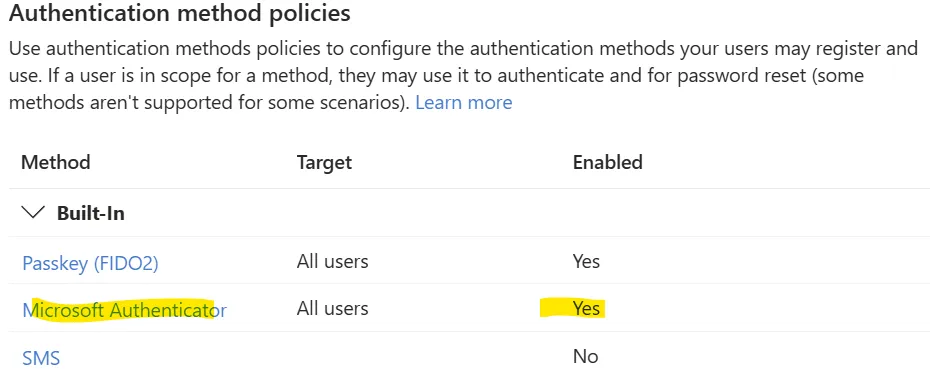
- Select Authentication methods policy
- Choose Microsoft Authenticator
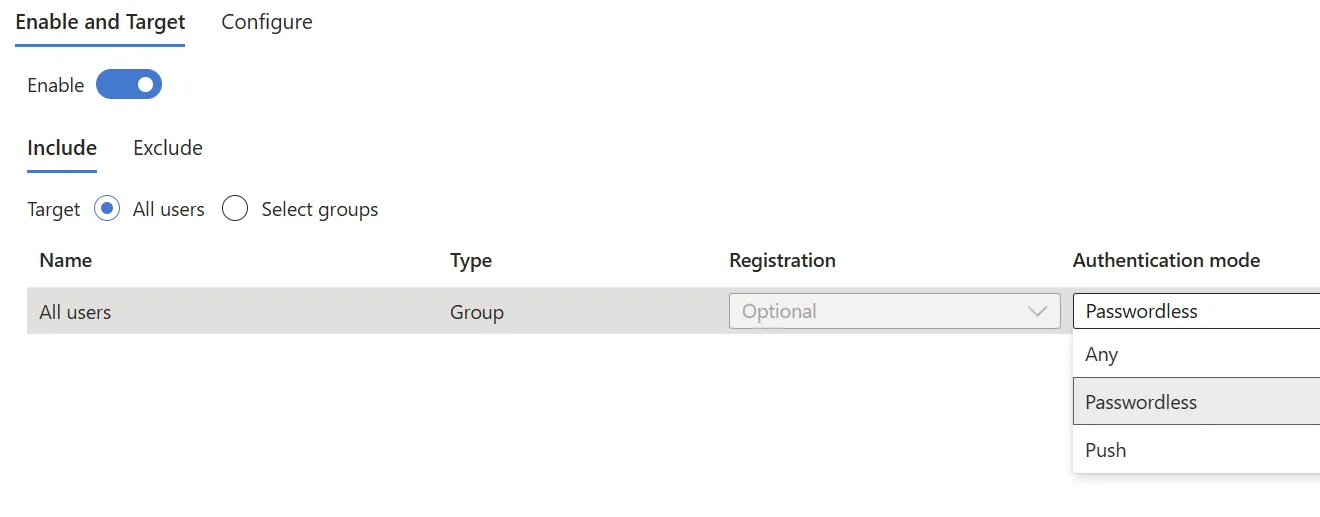
- Enable it for either All users or a pilot group
- Click Save
Step 2: User Setup with Microsoft Authenticator
Ask users to complete the following (if not already done):
- Install the Microsoft Authenticator app (not google or another authenticator app)
- [Computer] Visit https://mysignins.microsoft.com/security-info
- [Computer] Add a new sign-in method and select Authenticator app
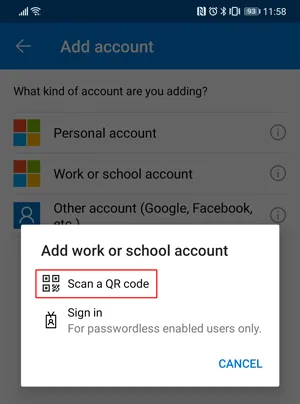
- [Phone] In the Authenticator app, select Add account -> Work or school account -> Scan a QR Code
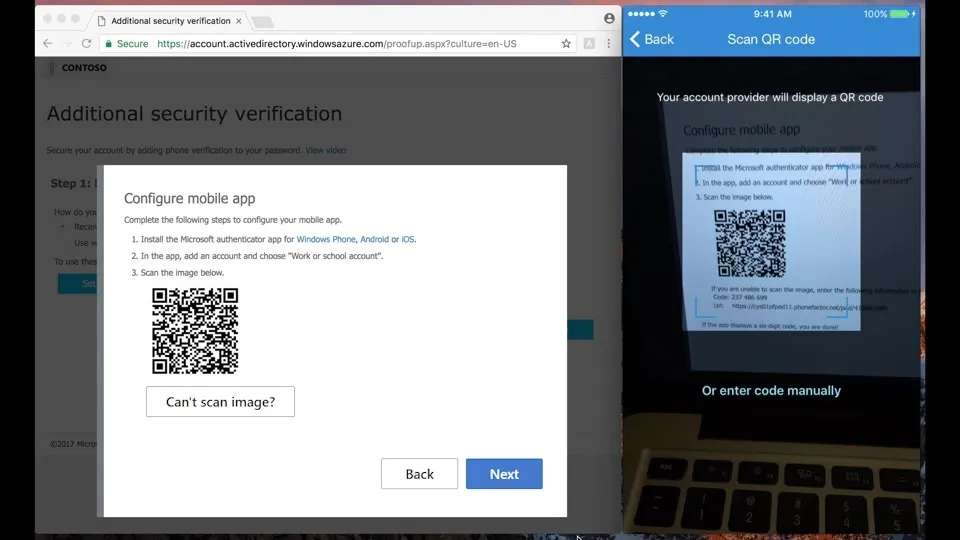
- [Phone] Scan the QR code and click Next in the computer browser
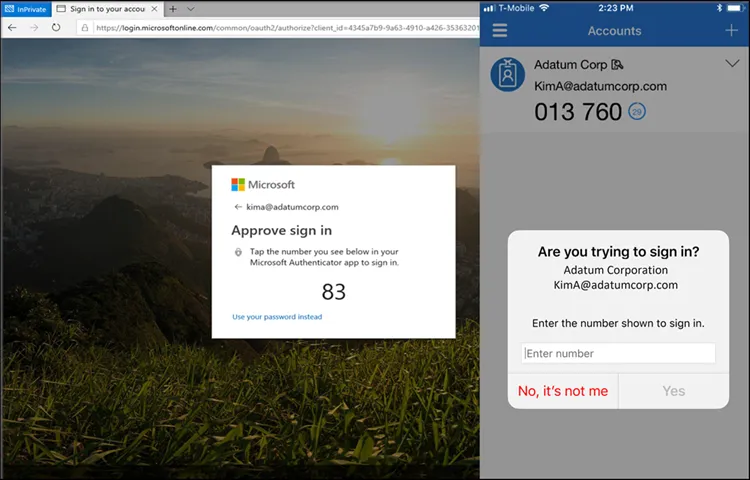
- [Phone] Confirm the authenticator push notification using the code on the computer
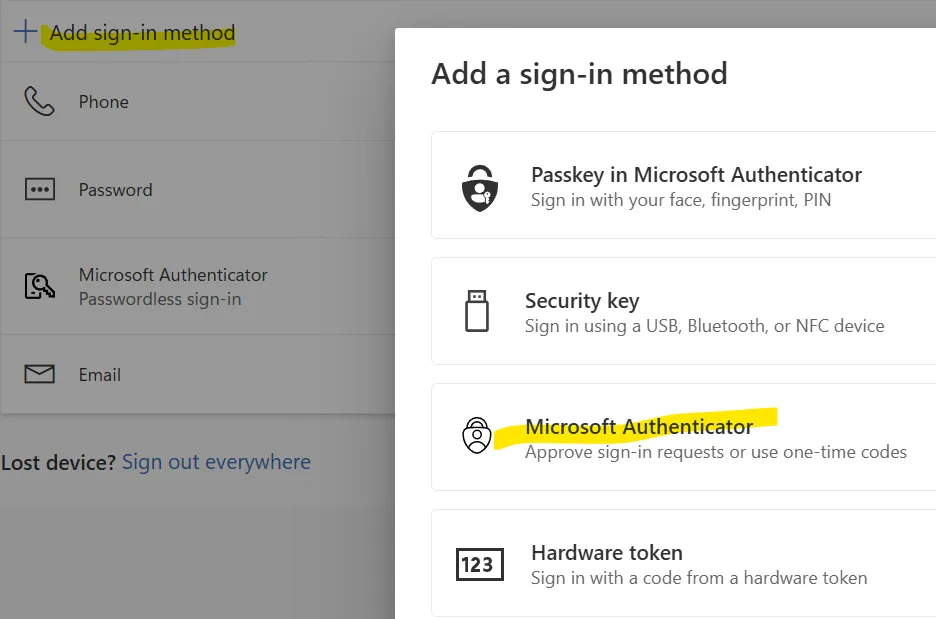
Initial Authenticator setup is complete! You can move on to turning on passwordless sign-in in Authenticator.
Enable Passwordless Sign-In in Authenticator
Next we will turn on passwordless sign in for the account in Microsoft Authenticator
- On your phone, find the account you added to Microsoft Authenticator and tap it
- Tap "Set up Passwordless sign-in requets"
- Sign into your Microsoft Account - this will be the last time you'll use this password
- Register your device. You won't be able to use passwordless sign in until you do this.
- You are all done, you should see under the account "Passwordless sign-in requests"
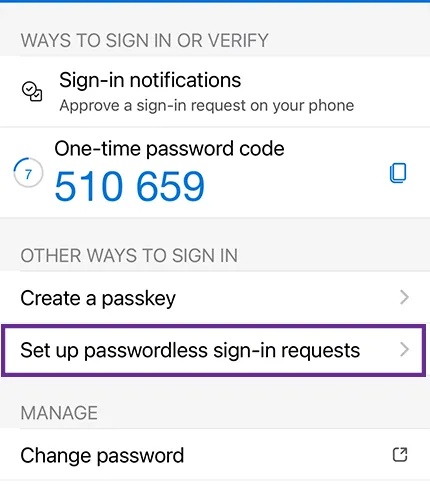
Turn on Web Sign-in for Windows 11 (optional, but recommended if you have Entra joined devices)
- Requirements are Windows 11 (22h2 or newer), Entra joined, and Microsoft Authenticator installed
You have a few options to turn this on, Intune, or deploy/install a ppkg file
Intune
- Go to https://intune.microsoft.com
- Navigate to Devices, and click on Configuration under the Manage Devices section
- Create a new policy
- For the Platform, select Windows 10 or later and the Settings catalog profile type
- Select the Authentication category
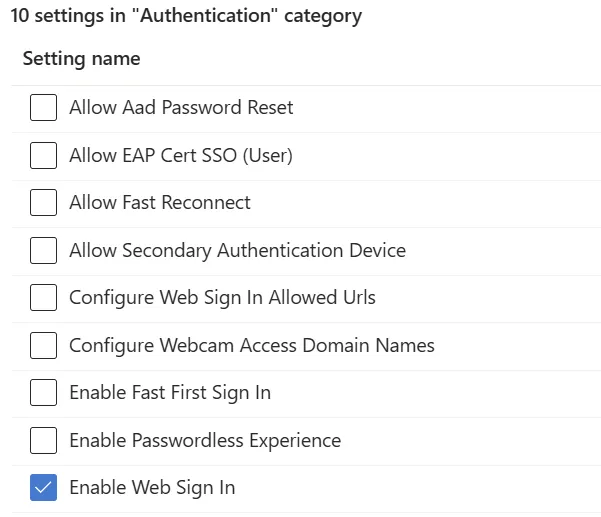
- Check the box for "Enable Web Sign-in"
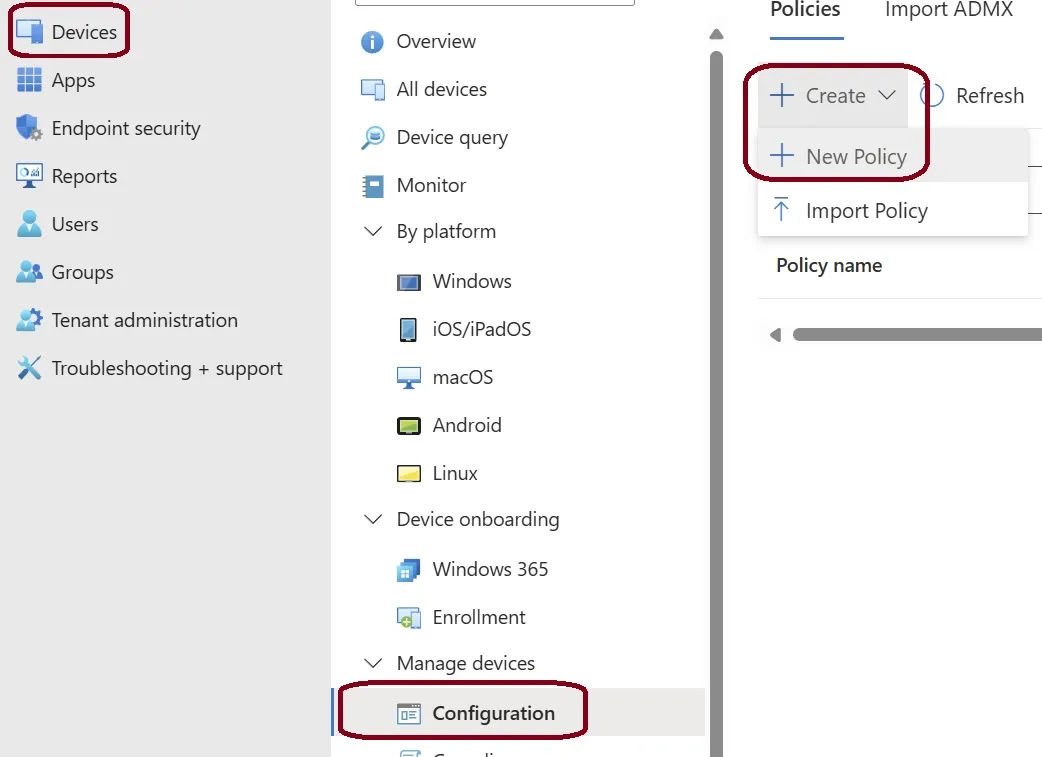
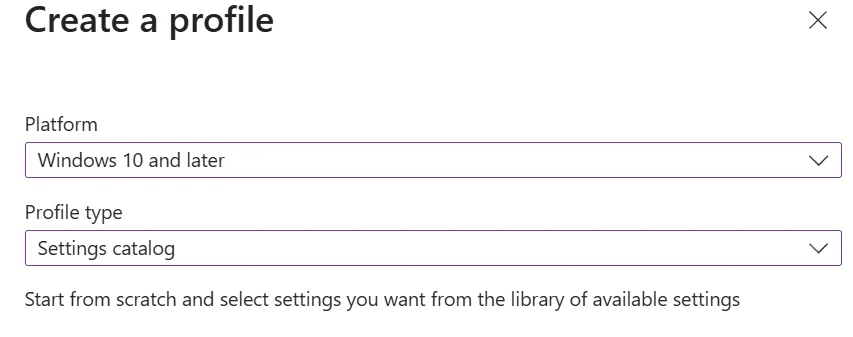
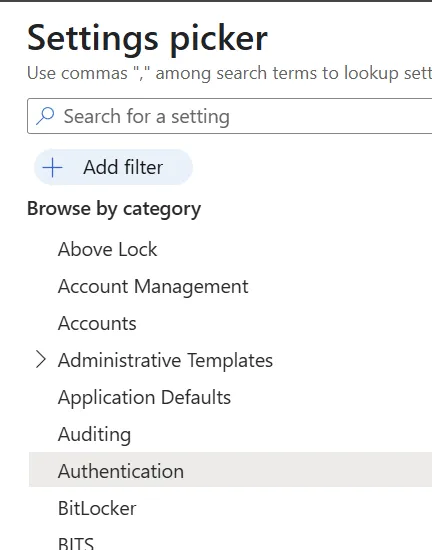
ppkg file
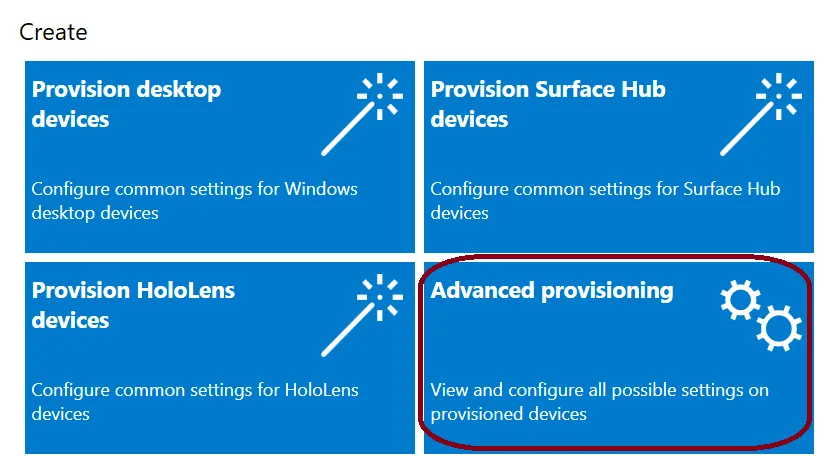
You will need the Windows Configuration Designer app, available in the Microsoft Store.
- Open the app and click on "Advanced Provisioning"
- Enter a name for your project and take note of the directory it is going to create the project in. Click Next
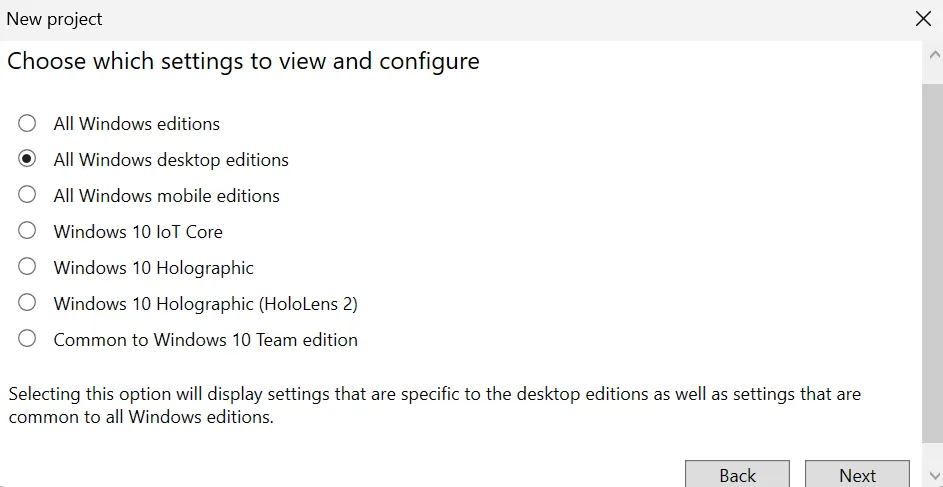
- Select "All Windows Desktop editions" and click Next. Skip the import a provisioning package step. Click Finish.
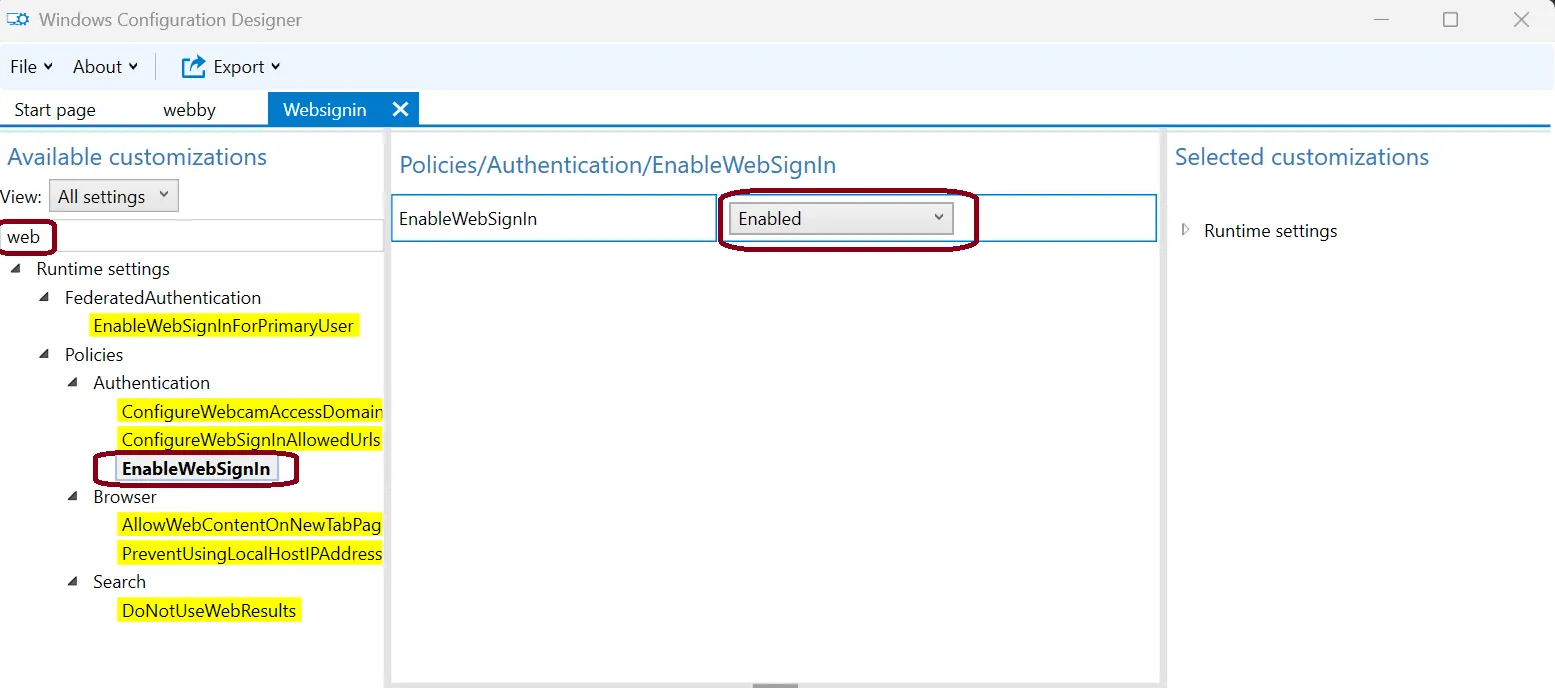
- You will now see the advanced view with a left hand pane of settings. In the search bar type "web". Select "Enable Web Sign-in". Click the drop down and select Enable.
- Export your project as a ppkg file. Click Next, Next, Next then Build. You will find the ppkg in the project folder
You can now install this ppkg file either by double clicking, or using powershell etc. There is no reboot required.
Step 4: Monitor and Enforce
Track sign-ins via the Sign-in logs in Entra admin center. Use Conditional Access to require passwordless methods for specific apps or users.
Best Practices
- Start with a small pilot group
- Provide internal guides or training sessions
- Maintain fallback sign-in methods during rollout
- Regularly review audit logs and user feedback
- Have one or more break glass accounts for your admin(s). This should use multiple strong sign in methods like a FIDO key, authenticator app, passkey etc.
Conclusion
Passwordless authentication is the future of secure access. Microsoft 365 and Entra ID make it easy to transition with minimal disruption. If you're a business in Calgary or Vancouver or elsewhere in Canada and need help configuring passwordless access, contact Huntertech. Our team provides expert IT solutions and cybersecurity services tailored to your needs.
Helpful Links
- Microsoft Entra ID Passwordless Authentication Options - Overview of all passwordless authentication methods available in Microsoft Entra ID
- Enable Phone Sign-in with Microsoft Authenticator - Step-by-step guide for enabling phone-based passwordless authentication
- Windows Web Sign-in - Detailed documentation on configuring Web Sign-in for Windows 11 devices
- Create a Provisioning Package - Guide for creating and deploying provisioning packages for Windows configuration
